- Phrack Magazine: Digital hacking magazine.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
Tuesday, June 30, 2020
Top 9 Best Websites To Learn Ethical Hacking 2018
re: please send me the Facebook traffic offer
17192961891667732136noreply
here it is, social website traffic:
http://www.mgdots.co/detail.php?id=113
Full details attached
Regards
Kiera Krajewski
Unsubscribe option is available on the footer of our website
Monday, June 22, 2020
re: How to remove a site from top 10 for important keywords
http://www.blackhat.to
Friday, June 19, 2020
re: I`m interested in your offer of Social Signals
omair1988.matoo
Glad to hear that, here are the details below
More information here:
http://www.realsocialsignals.co/buy-social-signals/
For the best ranking results, buy Monthly basis Social signals, provided
daily, month after month:
http://www.realsocialsignals.co/custom-social-signals/
Regards
Jose
http://www.realsocialsignals.co/unsubscribe/
2018-11-9, tr, 19:37 omair1988.matoo <omair1988.matoo@blogger.com> raše:
Hi there, Please send me the Social signal*s offer that% we talke%d about
over the phone. I`m interested and I want to boost my SEO metrics with this
new SEO method. Thanks again, will wait your reply.
Thursday, June 18, 2020
re: Additional Details
After checking your website SEO metrics and ranks, we determined
that you can get a real boost in ranks and visibility by using
aour 49 usd / Economy Plan:
https://www.hilkom-digital.com/product/economy-seo-plan/
thank you
Mike
Thursday, June 11, 2020
How To Crack A Password
What is Password Cracking?
Password cracking is the process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords. In other words, it's an art of obtaining the correct password that gives access to a system protected by an authentication method.
Password cracking employs a number of techniques to achieve its goals. The cracking process can involve either comparing stored passwords against word list or use algorithms to generate passwords that match
In this Tutorial, we will introduce you to the common password cracking techniques and the countermeasures you can implement to protect systems against such attacks.
Topics covered in this tutorial
- What is password strength?
- Password cracking techniques
- Password Cracking Tools
- Password Cracking Counter Measures
- Hacking Assignment: Hack Now!
What is password strength?
Password strength is the measure of a password's efficiency to resist password cracking attacks. The strength of a password is determined by;
- Length: the number of characters the password contains.
- Complexity: does it use a combination of letters, numbers, and symbol?
- Unpredictability: is it something that can be guessed easily by an attacker?
Let's now look at a practical example. We will use three passwords namely
1. password
2. password1
3. #password1$
For this example, we will use the password strength indicator of Cpanel when creating passwords. The images below show the password strengths of each of the above-listed passwords.
Note: the password used is password the strength is 1, and it's very weak.
Note: the password used is password1 the strength is 28, and it's still weak.
Note: The password used is #password1$ the strength is 60 and it's strong.
The higher the strength number, better the password.
Let's suppose that we have to store our above passwords using md5 encryption. We will use an online md5 hash generator to convert our passwords into md5 hashes.
The table below shows the password hashes
| Password | MD5 Hash | Cpanel Strength Indicator |
|---|---|---|
| password | 5f4dcc3b5aa765d61d8327deb882cf99 | 1 |
| password1 | 7c6a180b36896a0a8c02787eeafb0e4c | 28 |
| #password1$ | 29e08fb7103c327d68327f23d8d9256c | 60 |
We will now use http://www.md5this.com/ to crack the above hashes. The images below show the password cracking results for the above passwords.
As you can see from the above results, we managed to crack the first and second passwords that had lower strength numbers. We didn't manage to crack the third password which was longer, complex and unpredictable. It had a higher strength number.
Password cracking techniques
There are a number of techniques that can be used to crack passwords. We will describe the most commonly used ones below;
- Dictionary attack– This method involves the use of a wordlist to compare against user passwords.
- Brute force attack– This method is similar to the dictionary attack. Brute force attacks use algorithms that combine alpha-numeric characters and symbols to come up with passwords for the attack. For example, a password of the value "password" can also be tried as p@$$word using the brute force attack.
- Rainbow table attack– This method uses pre-computed hashes. Let's assume that we have a database which stores passwords as md5 hashes. We can create another database that has md5 hashes of commonly used passwords. We can then compare the password hash we have against the stored hashes in the database. If a match is found, then we have the password.
- Guess– As the name suggests, this method involves guessing. Passwords such as qwerty, password, admin, etc. are commonly used or set as default passwords. If they have not been changed or if the user is careless when selecting passwords, then they can be easily compromised.
- Spidering– Most organizations use passwords that contain company information. This information can be found on company websites, social media such as facebook, twitter, etc. Spidering gathers information from these sources to come up with word lists. The word list is then used to perform dictionary and brute force attacks.
Spidering sample dictionary attack wordlist
1976 <founder birth year>
smith jones <founder name>
acme <company name/initials>
built|to|last <words in company vision/mission>
golfing|chess|soccer <founders hobbies
Password cracking tool
These are software programs that are used to crack user passwords. We already looked at a similar tool in the above example on password strengths. The website www.md5this.com uses a rainbow table to crack passwords. We will now look at some of the commonly used tools
John the Ripper
John the Ripper uses the command prompt to crack passwords. This makes it suitable for advanced users who are comfortable working with commands. It uses to wordlist to crack passwords. The program is free, but the word list has to be bought. It has free alternative word lists that you can use. Visit the product website http://www.openwall.com/john/ for more information and how to use it.
Cain & Abel
Cain & Abel runs on windows. It is used to recover passwords for user accounts, recovery of Microsoft Access passwords; networking sniffing, etc. Unlike John the Ripper, Cain & Abel uses a graphic user interface. It is very common among newbies and script kiddies because of its simplicity of use. Visit the product website http://www.softpedia.com/get/Security/Decrypting-Decoding/Cain-and-Abel.shtml for more information and how to use it.
Ophcrack
Ophcrack is a cross-platform Windows password cracker that uses rainbow tables to crack passwords. It runs on Windows, Linux and Mac OS. It also has a module for brute force attacks among other features. Visit the product website http://ophcrack.sourceforge.net/ for more information and how to use it.
Password Cracking Counter Measures
- An organization can use the following methods to reduce the chances of the passwords been cracked
- Avoid short and easily predicable passwords
- Avoid using passwords with predictable patterns such as 11552266.
- Passwords stored in the database must always be encrypted. For md5 encryptions, its better to salt the password hashes before storing them. Salting involves adding some word to the provided password before creating the hash.
- Most registration systems have password strength indicators, organizations must adopt policies that favor high password strength numbers.
Hacking Activity: Hack Now!
In this practical scenario, we are going to crack Windows account with a simple password. Windows uses NTLM hashes to encrypt passwords. We will use the NTLM cracker tool in Cain and Abel to do that.
Cain and Abel cracker can be used to crack passwords using;
- Dictionary attack
- Brute force
- Cryptanalysis
We will use the dictionary attack in this example. You will need to download the dictionary attack wordlist here 10k-Most-Common.zip
For this demonstration, we have created an account called Accounts with the password qwerty on Windows 7.
Password cracking steps
- Open Cain and Abel, you will get the following main screen
- Make sure the cracker tab is selected as shown above
- Click on the Add button on the toolbar.
- The following dialog window will appear
- The local user accounts will be displayed as follows. Note the results shown will be of the user accounts on your local machine.
- Right click on the account you want to crack. For this tutorial, we will use Accounts as the user account.
- The following screen will appear
- Right click on the dictionary section and select Add to list menu as shown above
- Browse to the 10k most common.txt file that you just downloaded
- Click on start button
- If the user used a simple password like qwerty, then you should be able to get the following results.
- Note: the time taken to crack the password depends on the password strength, complexity and processing power of your machine.
- If the password is not cracked using a dictionary attack, you can try brute force or cryptanalysis attacks.
Summary
- Password cracking is the art of recovering stored or transmitted passwords.
- Password strength is determined by the length, complexity, and unpredictability of a password value.
- Common password techniques include dictionary attacks, brute force, rainbow tables, spidering and cracking.
- Password cracking tools simplify the process of cracking passwords.
12 Ways To Hack Facebook Account Passwords And Its Proeven Tion Techques 2020
Being a FB white hat hacker, I get following questions frequently from people:
- Can you refer any reliable Facebook hacker? (After me denying their hacking request 😛 )
- Is there any online FB cracker tool?
- Where can I get FB hacking software?
- Is there any free password finder?
- How can I hack someone's Facebook account easily?
To the best of my knowledge, there is no hacking tool. You won't be able to find it anywhere. However, you will find many websites claiming that they are providing free hack tool (either online or offline), but you cannot download the password file without completing a survey. Even after going through a tiresome process of completing a survey, you would have got nothing in the end. These things are posted only with the intention of making money. Don't waste your precious time in searching such hack tool.
If you want to know how hackers can hack someone's FB account, please go ahead and read the techniques listed below. The most successful method among all of these techniques is phishing. Phishing enables someone with no or little technical knowledge to hack account's password easily in just a few minutes.
Some of the techniques listed below are not applicable only to FB but also to all daily used internet websites, such as Google, Twitter, Yahoo etc.
You won't be vulnerable to hacking if you understand how hacking works
This article is written with the aim of educating people about how hacking works and how should they prevent it. Please don't use these techniques for malicious purposes.
1 Phishing
Phishing is the most common technique used for hacking FB passwords. It is very easy for someone who is having little technical knowledge to get a phishing page done. That is why phishing is so popular. Many people have become a victim of Phishing page due to its trustworthy layout and appearance.
How does phishing work?
In simple words, phishing is a process of creating a duplicate copy of the reputed website's page with the intention of stealing user's password, or other sensitive information like credit card details. In our topic, it means creating a page which perfectly looks like FB login page but in a different URL like fakebook.com, or faecbook.com, or any URL that pretends to be legit. When a user lands on such a page, he/she may think that is the real Facebook login page, asking him/her to provide his/her username and password. So, the people who do not find phishing page suspicious are going to enter their username & password. The password information will be sent to the hacker who created the phishing page. At the same time, the victim gets redirected to original FB page.
Example: John is a programmer. He creates an FB login page with some scripts that enable him to get the username and password information. John puts this fake login page in https://www.facebouk.com/make-money-online-tricks. Peter is a friend of John. John sends a message to Peter, "Hey Peter, I have found a free trick to make money online, you should definitely take a look at https://www.facebouk.com/make-money-online-tricks-free". Peter navigates to the link and see a FB login page. As usual, Peter enters his username and password on it.
The hacking part
The username and password of Peter is sent to John and Peter is redirected to a money making tips page https://www.facebouk.com/make-money-online-tricks-tips-free.html. That's all; Peter's Facebook account is hacked.
Please note that phishing is done by a third person through emails; that is how it happens most of the time. So always beware of phishing emails, else you may lose your Facebook account, or credit card details, or any other sensitive data. Learn more about phishing.
How can you protect yourself against online FB phishing?
Hackers can reach you in many ways; email, personal messages, FB messages, website ads etc. Clicking any links from these messages will lead you to a FB login page. Whenever you find an FB login page, you should note only one thing which is URL. Because nobody can spoof/use Facebook URL except when there are some XSS zero-day vulnerabilities, but that's very rare.
- What is the URL you see in browser address bar?
- Is that really https://www.facebook.com/ (Trailing slash is very important since it is the only separator in Google chrome to distinguish domain and subdomain. Check out the below examples to know the difference)?
- Is there a green color secure symbol (HTTPS) provided in the address bar?
Bearing these questions in mind should prevent you from the hacking of online phishing pages. Also, see the below examples of phishing pages.
Some super perfect phishing pages
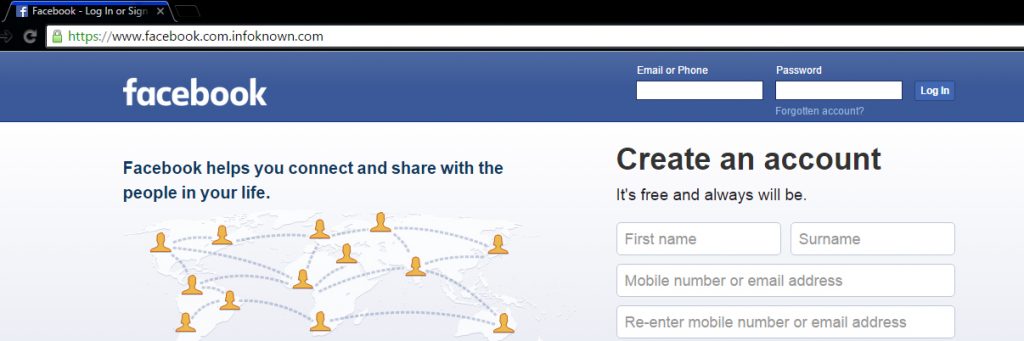
Most of the people won't suspect this page (snapshot given above) since there is an https prefix with a green color secure icon and also there is no mistake in www.facebook.com. But, this is a phishing page. How? Note the URL correctly. It is https://www.facebook.com.infoknown.com. So, www.facebook.com is a sub-domain of infoknown.com. Google Chrome does not differentiate the sub-domain and domain, unlike Firefox does.
One can obtain SSL Certificates (HTTPS) from many online vendors. A few vendors give SSL Certificate for Free for 1 year. It is not a big deal for a novice to create a perfect phishing page like the one given above. So, beware of it.
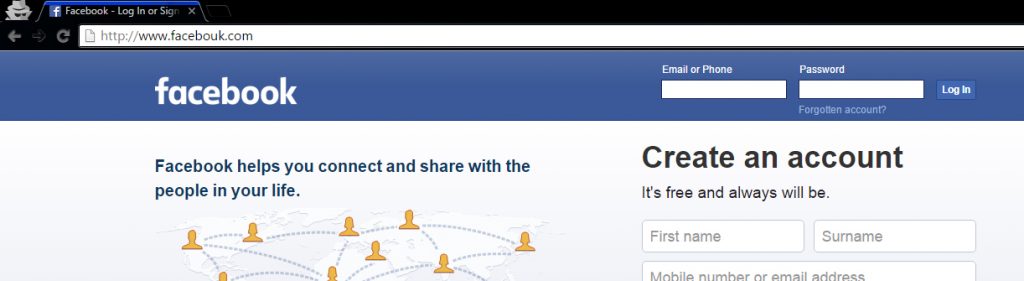
This is a normal FB Phishing page with some modification in the word Facebook.
2 Social Engineering
This is the second most common technique for hacking Facebook accounts. In fact, this method shouldn't come under Hacking, since much knowledge is not required for this method. I am listing this method under hacking to ensure the list of most common techniques used for FB account hacking in their respective order. Social engineering is basically a process of gathering information about someone, whose account you need to hack. The information may be his/her date of birth, mobile number, boyfriend/girlfriend's mobile number, nickname, mother's name, native place etc.
How does Social Engineering work?
Security Question
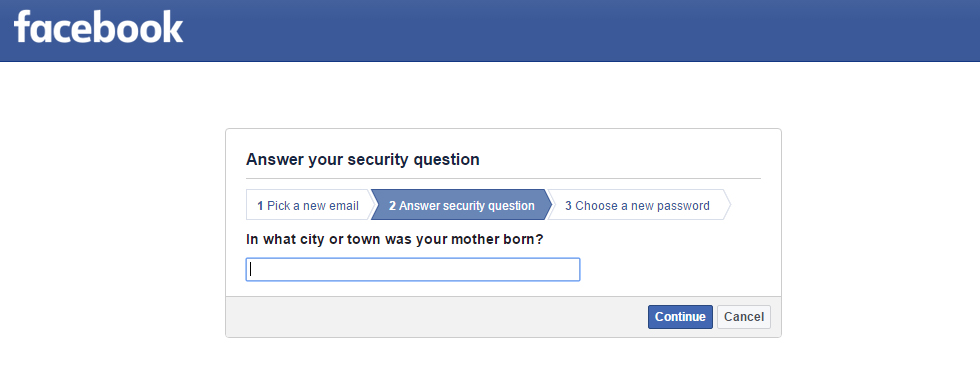
Many websites have a common password reset option called Security Question. Most common security questions are :
What is your nickname?
Who is your first-grade teacher?
What is your native place?
or
Any custom questions defined by the user.
Obtaining such information from the respective people may let us hack into their account. So, if anyone comes to know the answer to it, they will be able to hack your account using forgot password option.
Most Common and Weak Passwords
Security Question does not let you get into others FB account easily. But, setting a weak password could easily allow any of your friends to hack your account.
What is a weak password?
A password that is easily guessable by a third person is known as a weak password.
Most common passwords
- Mobile Number
- Nickname / Name and Date of Birth Conjunction
- Boy Friend's Mobile Number / Girl Friend's Mobile Number – Most of the lovers 😛
- Girl Friend's / Boy Friend's Name – Most of the lovers 😛
- Boy or Girl Friend Name Combination
- Bike Number
- Unused / Old Mobile Number
- Pet Name
- Closest Person Name (can be friends too)
Now, be honest and comment here if you are one of the people who have any one of the common passwords mentioned above. Please don't forget to change your password before making a comment 😉
How can you protect yourself from Social Engineering?
Security Question
Don't have a weak or familiar security question/answer. Therefore, it should be known only to you. You can set your security question here. Fortunately, Facebook has a lockout period of 24 hours before giving access to the one who successfully answered the security question, meaning that the hacker cannot enter into your account until 24 hours. So you can prevent the hacking attempt by logging in to your account in the 24 hours lockout period.
Additionally, FB provides an option called "Login Alerts" under Facebook Security Settings. You should add your mobile or email there to get notified whenever your account is logged in to a new or unknown device.
Most Common and Weak Passwords
It is very simple. Change your password now if you have any one of the weak passwords stated above.
You might also be interested in hacking facebook fan page article
3 Plain Password Grabbing

This is another common method used to steal Facebook user's password. Most people are unaware of this method, but traditional hackers use this method to hack user accounts.
How does Plain Password Grabbing works?
In this method, the Facebook hacker targets a particularly low-quality website, where the victim is a member and hacks their database to get the stored plain username & password of victim.
How could the hacker/attacker get access to Facebook?
Many of us use the same password for FB and also for some poor xyz.com. So, it is easy for a hacker to get your password through the low-quality poorxyz.com.
In another scenario, the hacker/attacker creates a website with the intention of getting victim's password, so when the victim registers his/her account using email and creates a password, those details will get stored in the database of the hacker/attacker. Thus hacker gets access to victim's account.
Common people, who use same email and password for these kinds of low-quality websites, may end up losing their Facebook account.
How can you protect yourself from Facebook Plain Password Grabbing?
You should never trust the third party low-quality websites. Even passwords of popular websites, like LinkedIn, are insecure and vulnerable to hacking. So, never and ever trust the third party low-quality websites.
Most of the website developers are storing plain passwords in their database without even thinking about encryption or security. This makes Facebook hackers' job easy since the password is in plain text format.
Best way to prevent this method is to have a unique password at least for websites that you really trust. Don't use your FB password for any other website/portal, so your password will be safe .
4 Key Logger

A keylogger is a software tool used to record keystrokes on a computer or mobile device. This, in turn, records everything you type using your keyboard and store it for use. Generally, keyloggers are installed as application software in operating systems to track keystrokes, but there are hardware keyloggers as well.
Hardware keyloggers also are known as physical keyloggers attached to a computer in a USB port records everything before it sends the keyboard data to the computer. There are various mobile keyloggers, that perform the same action on various operating systems.
How Key Logging works?
All keyloggers run in the background (except trial versions) and won't be viewable to users until you know the keylogger password and shortcut used to view it. It will record all the keys pressed and give you a detailed report of when and what keys are used for what application – Simply, a clean report to identify passwords.
Anyone who is reading the keylogger logs is able to see the Facebook password or any passwords and sensitive information typed, like credit cards, bank username, password etc. Whenever you log in to a public computer, there are chances to lose your Facebook password to someone else.
Hardware keyloggers are identifiable in case of your personal computer but are hard in case of public computers.
In another scenario, your friend/colleague/neighbor could ask you to log in using their computer as a help. If their intention is to get your password, then you are most likely to lose your Facebook account to the hacker.
Nowadays, many people are using mobile keyloggers. It enables to track the keypad of mobile. So, any sensitive information typed on the mobile keypad is vulnerable to hacking.
How can you protect yourself from Key Logging?
You need not be afraid of keyloggers when you use your personal computer since you are the only one who is going to access it. But, whenever you use any public computer or your friend's computer, you should not trust it.
I always suggest my friends use On-Screen Keyboard whenever they are in need to type a password. Also, please make sure that nobody is checking your screen when you type your password because your screen would expose what you had typed. In windows, there is an inbuilt tool called On-Screen Keyboard that helps us to select keys using the mouse.
You can open OSK by using the Run dialog box. Winkey + R to open Run dialog box, type OSK and then press Enter. Nowadays, many banking portals provide a screen keyboard in the browser itself. So, please make use of it whenever you are surfing on public computers. On-Screen Keyboard helps even when hardware keyloggers are installed.
Never use third-party mobile keypad apps unless you really trust the publisher because the app may track all of your keystrokes and send it to the publisher.
5 Browser Extension Hacker
This method doesn't let the Facebook hacker/attacker gain complete access to your Facebook account, however, gives some power to control your account indirectly. I've seen multiple Google Chrome and Firefox add-ons, which secretly perform actions, like following a person, like a page on behalf of your Facebook profile, etc.
How Browser extension hack works?
When you visit some malicious websites or web pages, you will be prompted to install a browser add-on. Once you install the add-on, it will perform all the tasks described by the hacker or attacker who created it. Some primary actions are posting status updates on your wall, liking an FB page, following a person, adding you to some Facebook groups, inviting your friends to like a page, or join a Facebook group etc. You may not know these things happening on your FB account until you check your Facebook activity log periodically.
How can you prevent browser extension Facebook hack?
You should monitor your activities using Activity Log. You must not trust any third party websites prompting you to add a browser extension. Install add-on only from the browser store, that too only from trusted publishers. Why should you risk your account if you don't know the publisher or intention of the add-on? Therefore, always stay away from these malicious browser extensions.
6 Malicious Application Hack
Always remember that all the apps you use on Facebook are owned by third-party publishers and not by Facebook. Of course, there are a few exceptions like Instagram. A malicious application, which is requesting your permission, will do almost all kind of spam stuff on your Facebook profile.
How malicious application hack works?
Whenever you find Login using the Facebook option on any website, you should come to know that it is a third party Facebook application not owned by Facebook. When you click Login using Facebook, you will be shown a permission dialog box with the requested permission details. Once you click okay button, the requested personal details can be accessed from FB or the requested actions can be performed in your FB account on your behalf.
What could a third party application do on your Facebook account?
- Post photos and status update
- Share link to your timeline or to any group you belong
- Manage your page
- Post on behalf of you on the Facebook pages you own
- Access your personal information
- Access your photos including "Only me" privacy photos; sometimes they can further access your mobile photos using a Facebook vulnerability like the one I found (Don't worry, it's completely fixed now 😉 ).
These are just examples of what can be done. What if the application you are using is malicious? It could spam your Facebook account with a bunch of worthless contents.
How can you prevent yourself from malicious application hack?
You should always beware of what permissions you give to a Facebook application even though FB is reviewing application's permission requests. Don't give permission to an application if you don't trust the website or application.
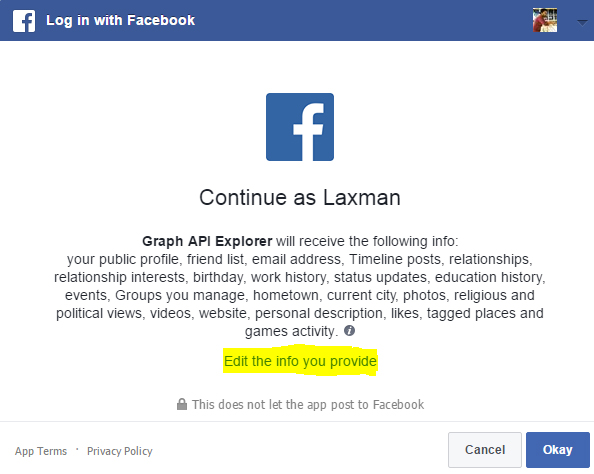
You can edit the information that you give to an application in the permission dialog box (snapshot given above). Also, you should review the applications that have access to your Facebook account here if you think you had given access to malicious applications.
7 Facebook Account Hacker Software
You might have seen or downloaded many Facebook account hacker software, but none of them could truly hack Facebook password. Hacking your Facebook password instead of the target user is what it actually does.
How does Facebook account hacker software work?
People who try to hack Facebook account usually download software that is available on various websites. The software will collect the victim's password (the one who downloaded this software) as soon as it is opened or installed. Some software prompt you to enter Facebook username and password. They will store your password in their database collection of passwords. Few other software gain administrative privilege from you to install background keylogger to get your keystrokes including the Facebook password.
How can you prevent yourself from Facebook hacking software?
Don't trust Facebook hacking software. There is no real hacking software available on the Internet as I had said earlier.
8 Malicious Mobile Application
There are a lot of mobile applications that secretly steal Facebook access token from your mobile device. Facebook mobile app functions through API, where access-token stored in your mobile's internal memory is used for authentication. It is more like your username and password. So, if someone steals your access-token, then he/she is likely to have full access to your Facebook account.
How malicious mobile application software works?
Facebook Application Interface do not require username or password every time to get user data. It just needs secret access-token to retrieve user's data. Facebook mobile app stores the access token in mobile's memory. The app's part of the memory is accessible only to the respective application. Mobile apps that have administrative privilege can access other app's data. For example, gaining admin privilege in a rooted android phone could allow an application to steal your access token. A hacker can do a lot of malicious things if he/she gets your access token.
How can you prevent yourself from malicious mobile applications?
- Install mobile apps only from trusted publishers.
- Don't root your mobile device.
- Logout Facebook from your mobile device frequently to get your access token expired.
- Change your Facebook password frequently.
9 Browser Vulnerabilities

Browser Vulnerabilities are security bugs, which exist in older versions of mobile and desktop browsers.
How does browser vulnerabilities work on Facebook hacking?
Most browser vulnerabilities are exploited through an older version of the browser since all the zero days are patched by browser vendor once it is reported by researchers around the world. For example, Browser Same Origin Policy Vulnerability could allow a hacker/attacker to read the response of any Page like facebook.com and could be able to perform any action on your Facebook account since they are able to read the response by accessing the Facebook origin. Android Chrome SOP bypass by Rafay Baloch is one such vulnerability that is affecting Android web-view in Android < 4.4.
How can you prevent yourself from browser vulnerabilities?
You should always update your browser and operating system once there is an update available. Keeping an older version always has many risk factors involved.
Self XSS is also known as Self Cross Site Scripting. XSS is basically a web security vulnerability, which enables hackers to inject scripts into web pages used by other users. What is self XSS then? Self XSS is a kind of social engineering attack, where a victim accidentally executes a script, thus exploiting it to the hacker.
How does self XSS scam work?
In this method, hacker promises to help you hack somebody else's FB account. Instead of giving you access to someone else's account, the hacker tricks you into running malicious Javascript in your browser console that gives a hacker the ability to manipulate your account. Facebook hackers use this technique to add you in groups, add your friends to the group, post on your wall, add your friends in comments etc.
How can you prevent yourself from self XSS?
Self XSS is something that you let hackers to hack your account. So never and ever copy & paste the code given by someone in your browser, otherwise, you will get your Facebook account hacked.
11 Trojan Horses
Trojan Horse is a malicious program, which is used to spy and control a computer by misleading users of its true intent. Malware Trojan can also be called as Remote Key Logger since it records keystrokes of all the applications of our computer and sends it to the hacker online.
How do Trojan Horses work?
A software you think legit might be a trojan. A PDF you don't suspect might contain a trojan. An AVI media file given by someone might be a trojan. The Trojan horse runs in the background process, collects information and send it to the hacker. Trojan Horse can be sent in any form through any medium, like pen drive, iPod, website, or email. In our topic, Trojan records FB password that you have typed in your browser and sends it to the Facebook hacker using the Internet.
How can you prevent yourself from Trojan?
- Do not
- install programs from unknown online sources
- play media files received from an unknown source
- open any kind of files downloaded from untrusted sources
- insert pen drive from any suspicious people.
- Do have an updated anti-virus software installed on your computer.
Keeping your anti-virus software up to date does not guarantee you to stay safe from hacking. Basically, an anti-virus software is a collection of detected malware and viruses. Its job is to compare each and every file with the database of viruses. There are many numbers of software, which enable us to create undetectable Trojans. But, it is very unlikely to target a common man with undetectable Trojanware. So, keeping an antivirus program up to date is protective to large extent. Don't forget to update your anti-virus software once an update is available.
12 FB Zero Day
Zero Day is a security vulnerability that is unknown to the respective software vendor. In our context, undiscovered Facebook vulnerabilities are called FB Zero Day.
How does Zero Day hacking work?
FB Zero Day vulnerabilities are very rare since Facebook has a bug bounty program, where security researchers around the world participate and report zero-day vulnerabilities. Zero-day is basically a security loophole that is unknown to the software vendor.
There are two types of people who find Zero Day vulnerabilities. The first case is Security Researchers and Bug hunters, who make a responsible disclosure about the vulnerability to the software vendor; FB in our context. Another case falls on the evil side. Blackhat hackers who find Zero Day vulnerabilities don't disclose it to Facebook and they will use it for their personal benefit of hacking.
@EVERYTHING NT
More infoRapidScan: The Multi-Tool Website Vulnerabilities Scanner With Artificial Intelligence
- One-step installation.
- Executes a multitude of security scanning tools, does other custom coded checks and prints the results spontaneously.
- Come of the tools include
nmap,dnsrecon,wafw00f,uniscan,sslyze,fierce,lbd,theharvester,dnswalk,golismeroetc executes under one entity. - Saves a lot of time, indeed a lot time!
- Checks for same vulnerabilities with multiple tools to help you zero-in on false positives effectively.
- Legends to help you understand which tests may take longer time, so you can Ctrl+C to skip if needed.
- Association with OWASP Top 10 2017 on the list of vulnerabilities discovered. (under development)
- Critical, high, large, low and informational classification of vulnerabilities.
- Vulnerability definitions guides you what the vulnerability actually is and the threat it can pose
- Remediations tells you how to plug/fix the found vulnerability.
- Executive summary gives you an overall context of the scan performed with critical, high, low and informational issues discovered. (under development)
- Artificial intelligence to deploy tools automatically depending upon the issues found. for eg; automates the launch of
wpscanandplecosttools when a wordpress installation is found. (under development) - Detailed comprehensive report in a portable document format (
*.pdf) with complete details of the scans and tools used. (under development)
For Your Infomation about RapidScan:
- Program is still under development, works and currently supports 80 vulnerability tests.
- Parallel processing is not yet implemented, may be coded as more tests gets introduced.
RapidScan supports checking for these vulnerabilities:
- DNS/HTTP Load Balancers & Web Application Firewalls.
- Checks for Joomla, WordPress and Drupal
- SSL related Vulnerabilities (HEARTBLEED, FREAK, POODLE, CCS Injection, LOGJAM, OCSP Stapling).
- Commonly Opened Ports.
- DNS Zone Transfers using multiple tools (Fierce, DNSWalk, DNSRecon, DNSEnum).
- Sub-Domains Brute Forcing.
- Open Directory/File Brute Forcing.
- Shallow XSS, SQLi and BSQLi Banners.
- Slow-Loris DoS Attack, LFI (Local File Inclusion), RFI (Remote File Inclusion) & RCE (Remote Code Execution).
- Kali Linux, Parrot Security OS, BlackArch... Linux distros that based for pentesters and hackers.
- Python 2.7.x
RapidScan's screenshots:
 |
| RapidScan helping menu |
 |
| RapidScan Intro |
 |
| RapidScan Outro |
How to contribute? If you want to contribute to the author. Read this.
Wednesday, June 10, 2020
Change Passwords Regularly - A Myth And A Lie, Don'T Be Fooled, Part 1
TL;DR: different passwords have different protection requirements, and different attackers using various attacks can only be prevented through different prevention methods. Password security is not simple. For real advise, checking the second post (in progress).
Are you sick of password advices like "change your password regularly" or "if your password is password change it to pa$$w0rd"? This post is for you!
The news sites are full of password advises nowadays due to recent breaches. When I read/watch these advise (especially on CNN), I am usually pissed off for a lot of reasons. Some advises are terrible (a good collection is here), some are good but without solutions, and others are better, but they don't explain the reasons. Following is my analysis of the problem. It works for me. It might not work for you. Comments are welcome!
Password history
Passwords have been used since ancient times.Because it is simple. When I started using the Internet, I believe I had three passwords. Windows login, webmail, and IRC. Now I have ~250 accounts/passwords to different things, like to my smartphone, to my cable company (this password can be used to change the channels on the TV), to my online secure cloud storage, to full disk encryption to start my computer,
Now, after this lengthy prologue, we will deep dive into the analysis of the problem, by checking what we want to protect, against whom (who is the attacker), and only after that, we can analyze the solutions. Travel with me, I promise it will be fun! ;)
What to protect?
Internet banking, online money
Credit card data
And sometimes, you are your own worst enemy. Don't do stupid things like this:
Work related passwords (e.g. Windows domain)
Email, social sites (Gmail/Facebook/Twitter), cloud storage, online shopping
They can use your account in Facebook votes. Your e-mail, cloud storage is again very important. 20 years ago you also had letters you didn't want to print and put in front of the nearest store, neither want you to do that with your private photo album. On a side note, it is best to use a cloud storage where even the cloud provider admin can't access your data. But in this case, with no password recovery option, better think about "alternative" password recovery mechanisms.
Other important stuff with personal data (e.g. your name, home address)
Not important stuff
This is the category other. I usually use one-time disposable e-mail to these services. Used for the registration, get what I want, drop the email account. Because I don't want to spread my e-mail address all over the internet, whenever one of these sites get hacked. But still, I prefer to use different, random passwords on these sites, although this is the "low level password" class.Attackers and attack methods
After categorizing the different passwords to be protected, let's look at the different attackers and attack methods. They can/will/or actively doing it now:Attacking the clear text password
This is the most effective way of getting the password. Bad news is that if there is no other factor of protection, the victim is definitely not on the winning side. The different attack methods are:- phishing sites/applications,
- social engineering,
- malware running on the computer (or in the browser),
- shoulder surfing (check out for smartphones, hidden cameras),
- sniffing clear-text passwords when the website is not protected with SSL,
- SSL MiTM,
- rogue website administrator/hacker logging clear text passwords,
- password reuse - if the attacker can get your password in any way, and you reuse it somewhere else, that is a problem,
- you told your password to someone and he/she will misuse it later,
- hardware keyloggers,
- etc.
The key thing here is that no matter how long your passwords are, no matter how complex it is, no matter how often do you change it (except when you do this every minute ... ), if it is stolen, you are screwed. 2FA might save you, or might not.
Attacking the encrypted password
This is the usual "hack the webserver (via SQL injection), dump the passwords (with SQLMap), post hashes on pastebin, everybody starts the GPU farm to crack the hashes" scenario. This is basically the only scenario where the password policies makes sense. In this case the different level of passwords need different protection levels. In some cases, this attack turns out to be the same as the previous attack, when the passwords are not hashed, or are just encoded.The current hash cracking speeds for hashes without any iterations (this is unfortunately very common) renders passwords like Q@tCB3nx (8 character, upper-lowercase, digit, special characters) useless, as those can be cracked in hours. Don't believe me? Let's do the math.
Let's say your password is truly random, and randomly choosen from the 26 upper, 26 lower, 10 digit, 33 special characters. (Once I tried special passwords with high ANSI characters inside. It is a terrible idea. Believe me.). There are 6 634 204 312 890 620 different, 8 character passwords from these characters. Assuming a 2 years-old password cracking rig, and MD5 hash cracking with 180 G/s speed, it takes a worst case 10 hours (average 5) to crack the password,
A lot of common hashing algorithms don't use protections against offline brute-force attacks. This includes LM (old Windows hashes), NTLM (modern Windows hashes), MD-5, SHA1-2-512. These hashing algorithms were not developed for password hashing. They don't have salting, iterations, etc. out of the box. In the case of LM, the problem is even worse, as it converts the lowercase characters to uppercase ones, thus radically decreasing the key space. Out of the box, these hashes are made for fast calculation, thus support fast brute-force.
Another attack is when the protected thing is not an online service, but rather an encrypted file or crypto-currency wallet.
Attacking the authentication system online
Attacking single sign on
Attacking 2FA
- one time tokens (SecurID, Yubikey) can be relayed in a man-in-the-middle attack,
- smartcard authentication can be relayed with the help of a malware to the attacker machine - or simply circumvented in the browser malware,
- text based (SMS) messages can be stolen by malware on the smartphone or rerouted via SS7,
- bio-metric protection is constantly bypassed,
- SSH keys are constantly stolen,
- but U2F keys are pretty good actually, even though BGP/DNS hijack or similar MiTM can still circumvent that protection,
- etc.
Others
Beware that there are tons of other attack methods to access your online account (like XSS/CSRF), but all of these have to be handled on the webserver side. The best you can do is to choose a website where the Bug Bounty program is running 24/7. Otherwise, the website may be full of low hanging, easy-to-hack bugs.Now that we have covered what we want to protect against what, in the next blog post, you will see how to do that. Stay tuned. I will also explain the title of this blog post.
More information
URLCrazy - Generate And Test Domain Typos And Variations To Detect And Perform Typo Squatting, URL Hijacking, Phishing, And Corporate Espionage
URLCrazy is an OSINT tool to generate and test domain typos or variations to detect or perform typo squatting, URL hijacking, phishing, and corporate espionage.
Homepage: https://www.morningstarsecurity.com/research/urlcrazy
Use Cases
- Detect typo squatters profiting from typos on your domain name
- Protect your brand by registering popular typos
- Identify typo domain names that will receive traffic intended for another domain
- Conduct phishing attacks during a penetration test
Features
- Generates 15 types of domain variants
- Knows over 8000 common misspellings
- Supports bit flipping attacks
- Multiple keyboard layouts (qwerty, azerty, qwertz, dvorak)
- Checks if a domain variant is valid
- Test if domain variants are in use
- Estimate popularity of a domain variant
Installation
Install from a package manager
If you are using Kali Linux, Ubuntu or Debian use:
$ sudo apt install urlcrazyInstall latest release
Visit https://github.com/urbanadventurer/urlcrazy/releases
Install current development version
Be aware the latest development version may not be stable.
$ git clone https://github.com/urbanadventurer/urlcrazy.gitInstall Ruby
URLCrazy has been tested with Ruby versions 2.4 and 2.6.
If you are using Ubuntu or Debian use:
$ sudo apt install rubyInstall Bundler
Bundler provides dependecy management for Ruby projects
$ gem install bundlerInstall Dependencies
$ bundle installAlternatively, if you don't want to install bundler, the following command will install the gem dependencies.
$ gem install json colorize async async-dns async-httpUsage
Simple Usage
With default options, URLCrazy will check over 2000 typo variants for google.com.
$ urlcrazy google.comWith popularity estimate
$ urlcrazy -p domain.comCommandline Usage
Usage: ./urlcrazy [options] domain
Options
-k, --keyboard=LAYOUT Options are: qwerty, azerty, qwertz, dvorak (default: qwerty)
-p, --popularity Check domain popularity with Google
-r, --no-resolve Do not resolve DNS
-i, --show-invalid Show invalid domain names
-f, --format=TYPE Human readable or CSV (default: human readable)
-o, --output=FILE Output file
-n, --nocolor Disable colour
-h, --help This help
-v, --version Print version information. This version is 0.7Types of Domain Variations Supported
Character Omission
These typos are created by leaving out a letter of the domain name, one letter at a time. For example, www.goole.com and www.gogle.com
Character Repeat
These typos are created by repeating a letter of the domain name. For example, www.ggoogle.com and www.gooogle.com
Adjacent Character Swap
These typos are created by swapping the order of adjacent letters in the domain name. For example, www.googel.com and www.ogogle.com
Adjacent Character Replacement
These typos are created by replacing each letter of the domain name with letters to the immediate left and right on the keyboard. For example, www.googke.com and www.goohle.com
Double Character Replacement
These typos are created by replacing identical, consecutive letters of the domain name with letters to the immediate left and right on the keyboard. For example, www.gppgle.com and www.giigle.com
Adjacent Character Insertion
These typos are created by inserting letters to the immediate left and right on the keyboard of each letter. For example, www.googhle.com and www.goopgle.com
Missing Dot
These typos are created by omitting a dot from the domainname. For example, wwwgoogle.com and www.googlecom
Strip Dashes
These typos are created by omitting a dash from the domainname. For example, www.domain-name.com becomes www.domainname.com
Singular or Pluralise
These typos are created by making a singular domain plural and vice versa. For example, www.google.com becomes www.googles.com and www.games.co.nz becomes www.game.co.nz
Common Misspellings
Over 8000 common misspellings from Wikipedia. For example, www.youtube.com becomes www.youtub.com and www.abseil.com becomes www.absail.com
Vowel Swapping
Swap vowels within the domain name except for the first letter. For example, www.google.com becomes www.gaagle.com.
Homophones
Over 450 sets of words that sound the same when spoken. For example, www.base.com becomes www.bass.com.
Bit Flipping
Each letter in a domain name is an 8bit character. The character is substituted with the set of valid characters that can be made after a single bit flip. For example, facebook.com becomes bacebook.com, dacebook.com, faaebook.com,fabebook.com,facabook.com, etc.
Homoglyphs
One or more characters that look similar to another character but are different are called homogylphs. An example is that the lower case l looks similar to the numeral one, e.g. l vs 1. For example, google.com becomes goog1e.com.
Wrong Top Level Domain
For example, www.trademe.co.nz becomes www.trademe.co.nz and www.google.com becomes www.google.org Uses the 19 most common top level domains.
Wrong Second Level Domain
Uses an alternate, valid second level domain for the top level domain. For example, www.trademe.co.nz becomes www.trademe.ac.nz and www.trademe.iwi.nz
Supported Keyboard Layouts
Keyboard layouts supported are:
- QWERTY
- AZERTY
- QWERTZ
- DVORAK
Is the domain valid?
URLCrazy has a database of valid top level and second level domains. This information has been compiled from Wikipedia and domain registrars. We know whether a domain is valid by checking if it matches top level and second level domains. For example, www.trademe.co.bz is a valid domain in Belize which allows any second level domain registrations but www.trademe.xo.nz isn't because xo.nz isn't an allowed second level domain in New Zealand.
Popularity Estimate
URLCrazy pioneered the technique of estimating the relative popularity of a typo from search engine results data. By measuring how many times a typo appears in webpages, we can estimate how popular that typo will be made when users type in a URL.
The inherent limitation of this technique, is that a typo for one domain, can be a legitimate domain in its own right. For example, googles.com is a typo of google.com but it also a legitimate domain.
For example, consider the following typos for google.com.
| Count. | Typo |
|---|---|
| 25424 | gogle.com |
| 24031 | googel.com |
| 22490 | gooogle.com |
| 19172 | googles.com |
| 19148 | goole.com |
| 18855 | googl.com |
| 17842 | ggoogle.com |
Known Issues
Macos File Descriptor Limit
If DNS resolution fails under Macos it could be due to the small default file descriptor limit.
To display the current file descriptor limit use:
$ ulimit -aTo increase the file descriptor limit use:
$ ulimit -n 10000URLCrazy Appearances
Kali Linux
URLCrazy was a default tool in BackTrack 5, and later Kali Linux. https://tools.kali.org/information-gathering/urlcrazy
The Browser Hacker's Handbook
Authored by Wade Alcorn, Christian Frichot, and Michele Orru.
URLCrazy is included in Chapter 2 of this seminal work on the topic.
PTES Technical Guidelines
Penetration Testing Execution Standard (PTES) is a standard designed to provide a common language and scope for performing penetration testing (i.e. Security evaluations). URLCrazy is included in the Tools Required section.
http://www.pentest-standard.org/index.php/PTES_Technical_Guidelines
Network Security Toolkit
Network Security Toolkit is a bootable Linux distribution designed to provide easy access to best-of-breed Open Source Network Security Applications. https://www.networksecuritytoolkit.org/
See Also
URLCrazy was first published in 2009, and for many years was the most advanced opensource tool for studying typosquatting. Since then multiple other tools have been developed by the infosec community.
DNSTwist
DNSTwist is developed by Marcin Ulikowski and first published in 2015. DNSTwist had a significant feature overlap with URLCrazy at the time, and introduced many new features.
Language: Python
https://github.com/elceef/dnstwist
URLInsane
URLInsane was developed by Rangertaha in 2018 and claims to match the features of URLCrazy and DNSTwist.
Language: Go
https://github.com/cybint/urlinsane
DomainFuzz
DomainFuzz was developed by monkeym4sterin 2017. Language: Node.JS
https://github.com/monkeym4ster/DomainFuzz
Authors and Acknowledgement
- Authored by Andrew Horton (urbanadventurer).
- Thanks to Ruby on Rails for Inflector which allows plural and singular permutations.
- Thanks to Wikipedia for the set of common misspellings, homophones, and homoglyphs.
- Thanks to software77.net for their IP to country database
Community
If you have any questions, comments or concerns regarding URLCrazy, please consult the documentation prior to contacting one of the developers. Your feedback is always welcome.
via KitPloit




























